Remote access VPN uses the following protocols:
- OpenVPN
- IKEv2/IPSec
- L2TP/IPSec
- WireGuard
- PPTP
- SSL/TLS
As companies are encouraging remote work in their workforce, remote access VPNs are being put forward for use. With this technology, people can access the company’s application and data remotely from afar over a secure network. Authorized employees can easily send and receive data on this network in encrypted format.
These software programs not only offer operational efficiency to the company but are also known for offering a secure network for sharing data. So, let’s move ahead and read all the aspects of remote access VPNs.
A remote access VPN is a virtual security solution that enables employees and contractors to connect to the company’s LAN and cloud networks remotely. This makes the connection easy to access, allowing users to access the data from their home or while travelling.
This type of VPN is needed when a small workforce is working remotely from their home or any other place. A company leverages VPN services to deploy VPN client software that allows users to build strong connections while sitting outside the network perimeter.
Depending upon the installation methods of the remote access VPN, there are mainly three different deployment types as mentioned below:
Following this, there are also some other cloud VPNs like IaaS that come with larger service packages but are not easy to deploy.
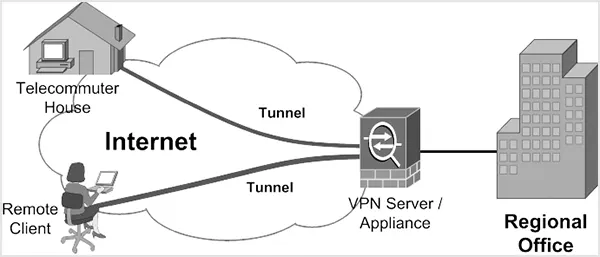
A remote access VPN creates an encrypted tunnel between the client and a VPN gateway/server/collector. This tunnel in the server protects all the information from unauthorized access by third parties.
Therefore, the remote users and their devices first need to qualify for the authentication. This requires the employees to bring their device to the office premises at once via the following ways:
When it comes to the easy authentication of the user, the client app method is the best, as it does not require any IT technician or administrator to build a tunnel to the server.
Opting for a remote access VPN comes with several benefits that can add a layer of assistance to your business’s effective management and security. So, let’s see what benefits remote access VPN offers to companies.
While counting on the benefits, neglecting the security concerns can internally damage your company by compromising its security. So, without any ado, hop into the security concerns of remote access VPN.
One of the most common confusions among companies when opting for a remote working VPN connection is choosing between a remote access VPN and a site-to-site VPN.
So, let’s dig deep and understand how these two are different, clarifying the doubts.
| Basis | Remote Access VPN | Site-to-Site VPN |
| Purpose | Connects individual users to a network. | Connects entire networks (e.g., two office locations). |
| Users | Used by remote workers or mobile users | Used by offices/branches |
| Setup | Requires VPN client software on the user’s device | Requires VPN gateways at both sites |
| Access | Provides user-to-network access | Provides network-to-network access |
| Security Access | Can include user authentication and device security checks | Typically, less user-level control |
Let’s now take a look at some of the alternatives to the remote access VPN that can help you decide on what suits your business best.
Digital workspaces come with a great ability to centralize the management of remote access to applications, leading to rapid adaptation by businesses. These digital workspace applications allow employees to utilize a limited number of tools and, in some cases, force the users to use only the vendor’s own application.
Although the digital workspace significantly improves the user experience, it lacks the encryption of the data that is shared digitally. Over and above that, these are also not very strong with remote access mechanisms, making them lose the race with remote access VPNs.
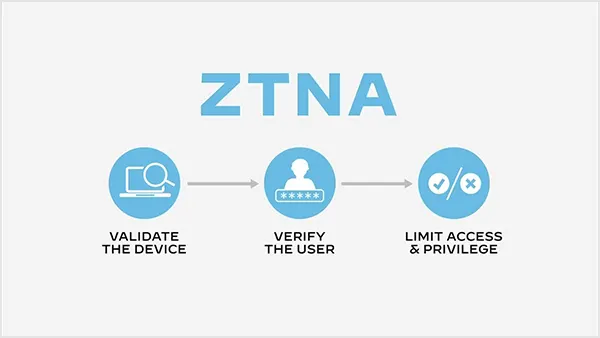
The latest innovation in the sector, the Zero Trust Network Access (ZTNA), strongly targets the network security of the connection via encryption, potent authentication, network segmentation, and monitoring.
Additionally, the security layers may include online threat detection and mitigation, two-factor authentication (2FA), robust access control, and even site-to-site VPN functionality.
Another great alternative to remote access VPN is the remote access software application, which allows the user to connect to an endpoint of the connection via the internet. However, the reason it failed to replace the remote access VPN is its lack of data encryption sent over the internet.
Moreover, these applications are not very user-friendly compared to remote access VPNs, except for some web-based software. Remember that these software programs hold the maximum risk of unauthorized third-party intervention, as the data is transferred in the raw format.
Remote access VPN is an invaluable tool that is being strategically used in companies to manage their workload from remote locations. These are the modern solutions to the risk-free workspace that streamlines the tasks and centralizes the management of the operations.
Even after delivering so much, remote access VPN still remains cost-effective for even small-scale companies.
Remote access VPN uses the following protocols:
The primary purpose of a remote access VPN is to enable users to connect to a private network remotely using a VPN.
Yes, the data shared on the remote access VPN tunnels is completely encrypted, serving the top level of security for the company’s confidential information.
Source: