The tunneling feature works by masking your IP address and creating an encrypted channel between your system and the VPN server for increased security.
What is a VPN Tunnel? Definition, Types, And How It Functions

The internet audience uses a VPN to enhance their digital security and increase their surfing speed while gaining access to certain geo-blocked websites. A VPN tunnel feature assists in establishing this by creating an encrypted channel to dispatch the user’s sent and received data.
VPN service providers apply two techniques to route the data through their encrypted connection, including full tunnel and VPN split tunneling. However, different service providers employ distinct tunneling protocols based on their security standards.
To understand in detail about the VPN tunnel, continue reading the detailed article to explore its necessity, along with its types and its working procedure.
What is a VPN Tunnel?

A VPN tunnel acts as an encrypted connection to establish a secure and private route between your device, where you are using the VPN, and the VPN server.
This process creates a secure, encrypted pathway that protects the data you send and receive during data transfer. A VPN tunnel is the core component of all VPNs, as it acts as a shield to protect your private data from cyber threats.
Its essential element of operation includes hiding the IP address to encrypt your data, which is impossible to crack without the use of a cryptographic key. This encrypted data is not accessible to your internet service providers (ISPs) or even the cyber criminals or attackers.
Also Read: Industrial Remote Access VPN: Secure Connectivity for Remote Operations
What Is The Purpose Of A VPN Tunnel, And How Does VPN Tunneling Work?
The major purpose of tunneling is to safeguard your data from interception and tracking. Since a VPN hides and disguises the user’s IP address, it requires tunneling protocols like OpenVPN or WireGuard to function.
While most of the VPN services promise a strict and transparent no-logs policy that signifies your data won’t be stored or accessed either by the VPN companies or by your Internet Service Providers.
However, the level of security these tunneling protocols offer differs with different service providers, depending on their security measures. To understand how a VPN tunnel exactly works, you can refer to these pointers.
- The first step involves connecting to your VPN service and choosing your preferred VPN server.
- Its next step includes the establishment of the tunnel, which is done by your VPN network through an encrypted channel using security protocols.
- The data that is now being transferred from your device is being encrypted before being released, which prevents it from being intercepted by attackers and your ISP.
- That released and encrypted data is received by the VPN server, which later decrypts it before delivering it to its planned destination.
- Lastly, the data that is sent from the website also passes through the same encrypted tunnel, which is later decrypted by your device. This helps in establishing security from both endpoints.
Also Read: Best Remote Access VPNs for Business – 5 Best Remote Access VPNs Listed
Categories of VPN Tunneling Protocols

VPN services offer different types of tunneling protocols based on their security resources. For instance, the Tunnel Bear VPN service uses WireGuard, OpenVPN, and IKEv2 protocols, while Webavior provides OpenVPN and 256-bit encryption for broad security.
However, each protocol provides different features, including speed, stability, and security. We have listed the primary types of VPN tunnel protocols below:
1. WireGuard
WireGuard is one of the highest-rated and most recommended choices for a tunneling protocol, since it’s among the fastest protocols that also offer high-level security.
It is a modern and the newest protocol that has a lightweight codebase consisting of just 4,000 lines. However, it is still a developing protocol, which requires its own infrastructure for encryption.
Due to its smaller codebase, it suits the needs of mobile users, while its modern cryptography assists in reducing risks for all major platforms, including Windows, macOS, Android, and iOS.
2. IKEv2/IPSec
IKEv2/IPSec is the combination of Internet Key Exchange version 2 (IKEv2) and Internet Protocol Security (IPSec), which provides a blend of high-speed features without compromising the security needs.
However, unlike Wireguard, it has a larger codebase of over 100,000 lines. It is incompatible with a few operating systems, yet it offers advanced features, including an auto-connect feature that helps in restoring interrupted connections.
3. OpenVPN
OpenVPN is one of the most popular security protocols among VPN users, since it is an open-source protocol that offers impressive security with its 256-bit encryption.
It has the largest codebase of around 600,00 lines, which also makes it a complex tunneling protocol. While it supports every major operating system, it runs primarily in two versions, including TCP and UDP.
4. PPTP
A PPTP or Point-to-Point Tunneling Protocol is the oldest tunneling protocol that is mostly considered unfit for use due to its security vulnerabilities.
While it is a simple and convenient protocol that offers impressive speed, it also possesses several risks caused by its weakest level of data encryption, which can be decrypted easily.
5. L2TP/IPsec
L2TP/IPsec is a combination of Layer 2 Tunneling Protocol (L2TP) and IPsec. It provides compatibility with almost every major platform, but its security features are a major concern.
It is an outdated protocol that is hardly being used these days by any service providers. L2TP/IPsec possesses several vulnerabilities to users’ data security, while it offers slower speeds as compared to other tunneling protocols.
6. SSTP
An SSTP or Secure Socket Tunneling Protocol is one of the highly secure protocols that provides secure encryption for high confidentiality. Since it doesn’t require the use of fixed ports, it is equipped with the capability of bypassing firewalls, including the Great Firewall of China.
While it provides distinctive security features and moderate speed, it lacks compatibility with all platforms except Windows. Since it was created by Microsoft, it is supported on Windows only.
What Is VPN Split Tunneling, And How Is It Different From Full Tunnels?
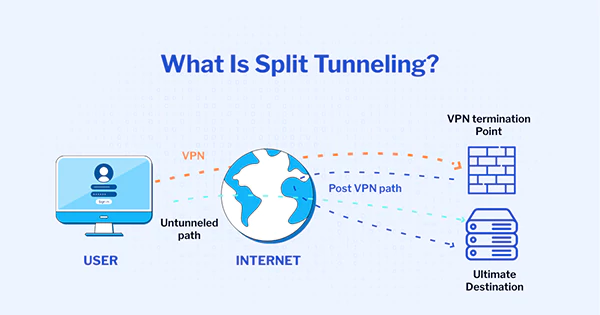
The split-tunnel VPN differs slightly from a full-tunnel VPN, as it is mainly used to establish a speedy connection. VPN split tunneling works by directing a portion of the user’s data through the encrypted pathway and sending the rest directly, eliminating the need for encryption and decryption.
It equips the user with a choice to choose which data should be transmitted through the encrypted tunnel and which should be sent directly. This feature significantly assists in gaining higher speeds for improved performance as compared to full tunnels.
However, while the split tunneling VPN feature proposes better speeds, it also brings security vulnerabilities. Since a full tunnel sends your whole internet traffic through its encrypted channel, it reduces the risk of cyber criminals gaining unauthorized access to your systems.
While VPN split tunneling is exposed to certain security risks, including the possibility of malware attacks. The transmitted data, which is not encrypted, can be tracked by your ISP and the government agencies. However, this split tunneling surely assists in a better gaming and streaming experience.
Also Read: What is SOAR and its Importance in the Digital Age? Explore all the Critical Components of Security!
Benefits of Using A VPN Tunnel

VPN tunneling is an important component of VPN service to enhance security and retain the user’s privacy. However, it possesses several other benefits, including:
- Added Security: The primary aim of a VPN tunnel is to provide users with advanced security against major threats, including data leaks and DDoS attacks. Since it masks the IP address and delivers the data through encryption, it creates a layer of security that acts as protection from cyber threats and man-in-the-middle attacks.
- Better Privacy: Along with enhancing security, it also contributes to maintaining the confidentiality and integrity of users’ private data. It also works in preserving your internet traffic from being tracked by your ISP or any third party.
- Improved Streaming and Gaming Experience: The tunneling feature contributes to enhancing the gaming and streaming experience by providing access to geo-blocked content that is probably unavailable in your region. It also helps in avoiding bandwidth throttling to achieve lag-free gaming.
- Enhanced Connectivity for Better Remote Operations: The tunneling feature helps in enhancing security to establish a secure connection for remote access through Remote Access VPNs. These services allow the remote employees to access the organization’s confidential data without worrying about a security breach.
Limitations and Risks Associated with a VPN Tunnel
The restrictions and risks involved with a VPN tunnel depend on the type of tunneling protocol used by the VPN server and your choice of encryption. A few of the risks and limitations involved with VPN tunnel include:
- While the split-tunneling VPN feature allows the service provider to deliver better speed to its users, it also exposes the user’s data to certain safety dangers, including data breaches and cyber attacks.
- Since the VPN tunnel’s primary function is to route internet traffic through a secure channel, it might result in relatively slower speeds while streaming or gaming. This mainly happens if your VPN service provider is using the full tunnel feature.
- A notable limitation is that it includes streaming and gaming limitations, as certain websites, such as Netflix, don’t support the use of VPN. Also, if they detect its usage, they can limit the user’s access to certain content.
Also Read: The Future of Remote Access: Is VPN Still the Best Solution?
Conclusion
A VPN tunnel is an essential component in enhancing your internet safety, as every activity that you perform on the web can be tracked by your ISP, government bodies, and even cybercriminals. The tunneling feature prevents this tracking by routing your transmitted data through an encrypted pathway.
It is advisable to opt for the best VPN service that ensures maximum privacy and provides the essential tunneling protocols for robust security.
FAQs
How does a VPN tunnel work?
Which is considered the best VPN tunnel protocol?
WireGuard is usually considered the foremost choice due to its speed and security features, while OpenVPN also offers impressive security with stable speed.
How is VPN split tunneling different from full tunnel VPNs?
A full tunnel functions by routing all of your internet traffic through its secured channel; however, split tunneling VPN servers transmit only partial data that is chosen by the user themselves.
